Normal surface blasting operations require AECI Mining Explosives to produce blast reports, actual measured hole depths, charging reports, etc. to be captured and documented. In some instances this exceeds ten pages of documented information.
BLAST-iTABLET is a software tool for use by our Field Representatives or Customer to reduce the amount of paper used on a site.
Users are identified by a username and password and assigned a level of authority.
Three levels of authority are catered for that restrict the functionality the user has access to. These restrictions are customisable by the responsible person for the site, mine or customer.
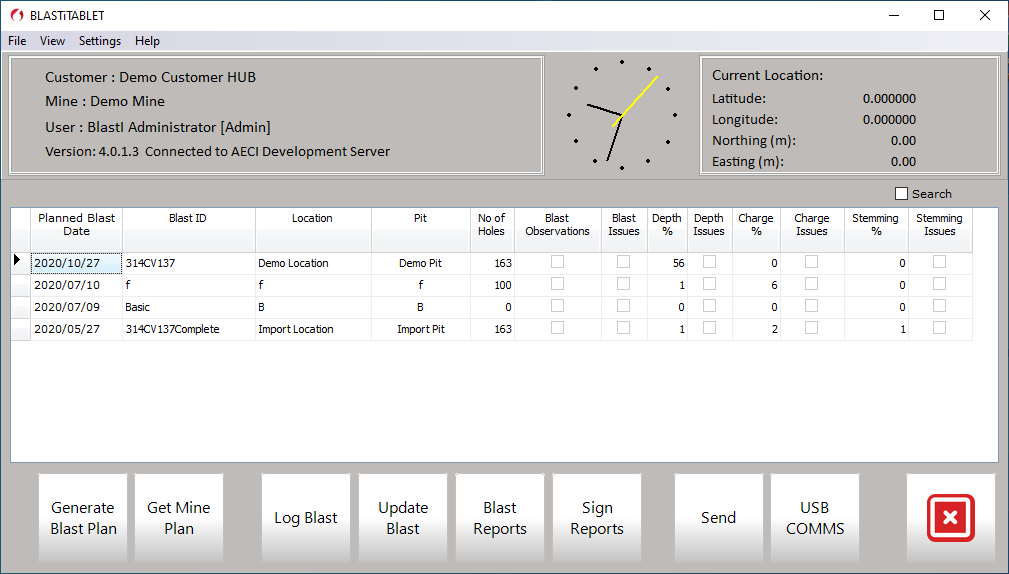
Data is captured either in a list view or a plan view of the blast plan depending on the user preference. All data captured is stored in a database that include an audit trail of who did what and when it was captured.
BLAST-iTABLET will graphically display the blast plan either from received co-ordinate based data or generated on-the-fly as a representation of the blast pattern. The co-ordinate based data import template is customisable to include various additional data like: planned hole depth, hole diameter, planned stemming length and planned explosives mass per hole.
The data capture currently catered for, include:
Data from multiple tablets on a single blast can be combined to include all data captured.
Reporting in a spreadsheet format is catered for and intended for the our Field Representatives to customise with additional graphs, etc. to meet their customer’s requirements.
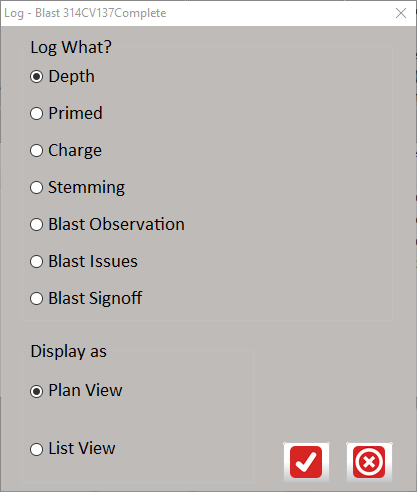
The main screen summarises the active blasts with an indication of progress for each. The progress indication is dependent on the latest available data at the given time.
Data is shared to a single responsible person for data management and combining the data received from multiple devices.
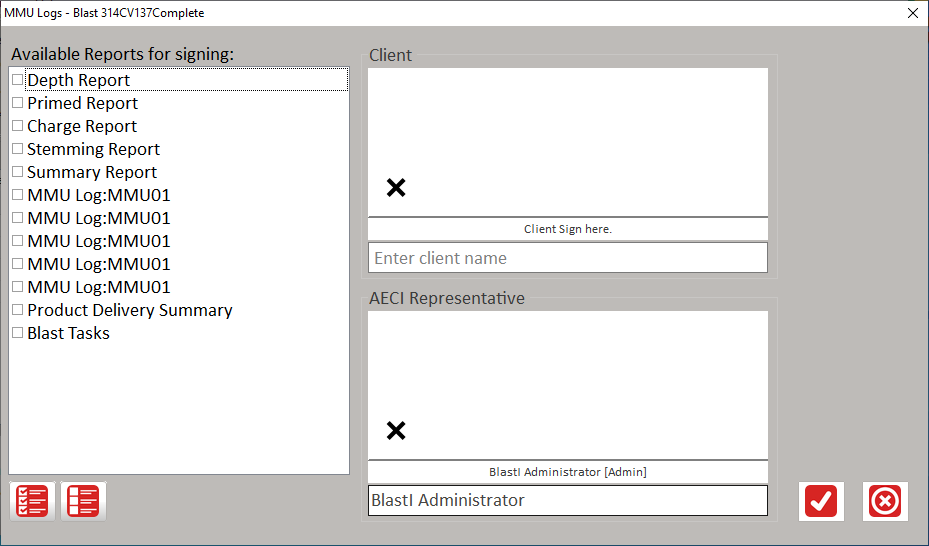
Reports are generated in pdf format for easy signing and sharing with the customer and include the following reports.
All reports can be generated at any time by a person whom has the necessary authority to do so.
All data captured is kept and therefore the integrity of the data is never compromised.
Minimum system requirements
Recommended system requirements